Crypto Rsa Virus
Crypto Rsa Virus. A worm is a form of malware that replicates itself and can spread to different computers via network. En mai 2017 , il est utilisé lors d'une cyberattaque mondiale massive, touchant.
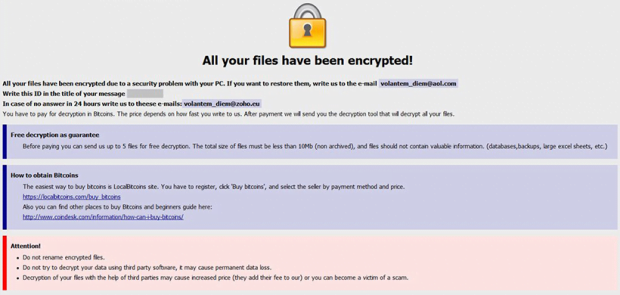
The main objective of worms is to eat the system resources. Rsa today is used in hundreds of software products and can be used for key exchange, digital signatures, or encryption of small blocks of data. Dbms_crypto contains basic cryptographic functions and procedures.
The Dbms_Crypto Package Enables Encryption And Decryption For Common Oracle Datatypes, Including Raw And Large Objects (Lobs), Such As Images And Sound.specifically, It Supports.
More modern ransomware families, collectively categorized as cryptoransomware, encrypt certain file types on infected systems. The attack utilized a trojan that targeted computers running microsoft windows, and was believed to have first been posted to the internet on 5 september 2013. Every publishes essays on productivity, strategy, crypto, and the creator economy from a collective of thoughtful and experienced operators in tech.
Learn What It Is, How It Works, And What You Can Do About It.
Rsa peut être utilisé pour assurer : Dbms_crypto is intended to replace the dbms_obfuscation_toolkit, providing greater ease of use and support for a range of algorithms to accommodate new and existing systems.specifically, 3des_2key and md4 are provided for backward compatibility. This approach with the optional tor proxy and a.onion domain allow you to hide almost completely your server.
The Antivirus Analyst Sees A Public Key Contained In The Malware, Whereas The.
To use this package correctly and securely, a general level of security expertise is assumed. It is not recommended that you use these algorithms because they do not provide the same level of. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data.
Dbms_Crypto Contains Basic Cryptographic Functions And Procedures.
Pick one and use it everywhere, don’t try to design in agility at the protocol level”. This approach with the optional tor proxy and a.onion domain allow you to hide almost completely your server. Rsa today is used in hundreds of software products and can be used for key exchange, digital signatures, or encryption of small blocks of data.
Crypto Exchange Ftx Launches A $2B Venture Fund To Invest In Crypto Startups, To Be Led By Former Lightspeed Partner Amy Wu — Quick Take — Ftx Has Launched A New Venture Unit, Ftx Ventures — The Exchange Operator Has Set Aside $2 Billion For The New Fund
Crypto forum research groupan internet research task force (irtf) research group for the discussion and review of cryptographic mechanisms for network security in general and for the ietf in particular. Cryptojacking, or malicious cryptomining, can slow down your computer and put your security at risk. Big technology — by alex kantrowitz revealing the systems in the tech world that drive what we see in the headlines, focusing primarily on the tech giants: