Asymmetric Crypto System
Asymmetric Crypto System. Cryptolocker is a malware threat that gained notoriety over the last years. The symmetric key is then encrypted with a public asymmetric key;
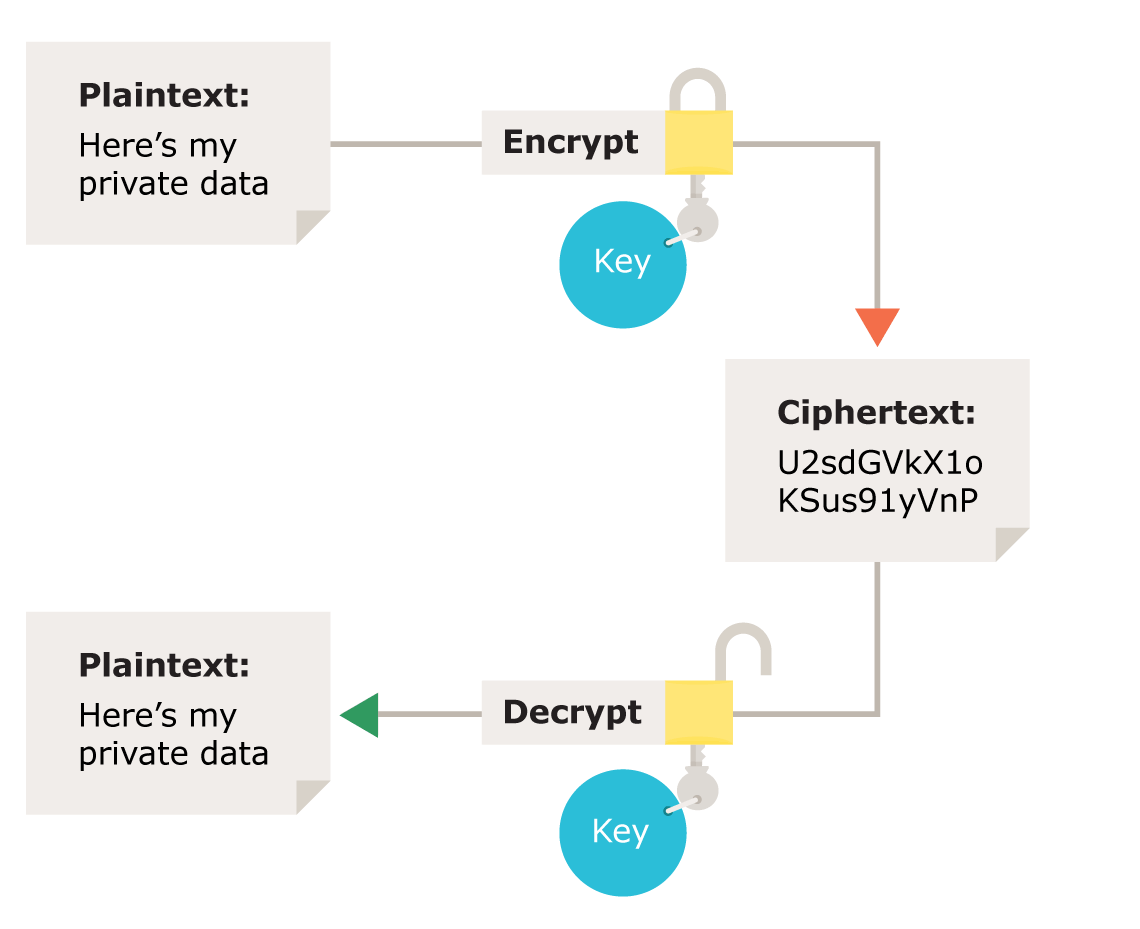
Cryptography means secret writing—the ability to exchange. A common question i often get from customers and students is about microsoft’s cryptographic service providers (csp). The javax.crypto.spec.ivparameterspec class can be used to initialize a cipher object with a given iv.
These Include Key Size, Mode Of Operation, Padding Scheme, Iv, Etc.
A sender and a recipient must already have a shared key that is known to both. This is a protocol within blockchain that. The <<strong>crypto</strong> permission class name> in the template above would actually be a specific permission class name, such as javax.crypto.cryptopermission.
Secure Random Is An Essential Requirement For Good Crypto Operations In Java.
Asymmetric encryption is mostly used when there are 2 different endpoints are involved such as vpn client and server, ssh etc. For example, if there are two keys “k1” and “k2”, then if key. This includes anything on your hard drives and all connected media — for example, usb memory sticks or any shared network drives.
It Is A Trojan Horse That Infects Your Computer And Then Searches For Files To Encrypt.
A crypto permission class reflects the ability of an application/applet to use certain algorithms with certain key sizes in certain environments. Asymmetric encryption uses two different keys as public and private keys. A common question i often get from customers and students is about microsoft’s cryptographic service providers (csp).
Confirming Identity For Someone To Sign A Document
Asymmetric encryption also called as private/public key encryption is a mathematical relation between two keys, one for encryption and the other for decryption. The public key can be shared with anyone, while the private key is meant to be kept secret to maintain security. The javax.crypto.spec.pbeparameterspec class can be used to initialize a cipher object implementing pbewithmd5anddes with a given salt and iteration count.
Network Encryption (Network Layer Or Network Level Encryption):
Linux kernel crypto api¶ author. The word “crypto” literally means concealed or secret. Cryptolocker is a malware threat that gained notoriety over the last years.